For some years now (as of April 2022), I have watched uninitiated downloading and uninitiated uploading, while plugged in to the internet through my home modem. I began taking screenshot evidence and labeling these files with the ongoing situation, on my Macs, (personal computers). All of my evidence for this writing is based on a built in Mac OS app called Activity Monitor, which actually has a more detailed user-interface than my screenshot images shared below. I display only the graphical data windows, screen shot live for evidence. Is it reliable evidence or not? I have heard half baked doubts which were insufficiently explained.
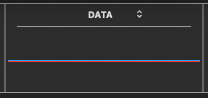
For this introductory post, I provide only a representative collection of images below, and wonder if others have observed equivalent activity uninitiated by themselves. I have collected together many suspicious incidents which were labeled by me, to ponder why these activities occur. There are plenty of observed moments when the network activity is flat lined, zero data in, zero data out, with blue line on top and red line underneath, as first image below:

In contrast to the flat line above, I wonder if the waveform-displays following below will be determinable as intrusive or worse. I have considered the possibility that most of the following patterns are signals to setup infiltration processes and override any PC privacy features. Please note that these detailed-waveforms were observed only with a plugged in network connection, through a modem with rural, copper wire telephone wires.
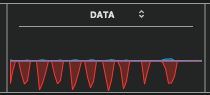
Image Below: Notice the tiny pulses to the left, in the following image. The blue color indicates incoming, low amplitude signals, as possible initial signs of increasing data reception, coming from the internet. The blue color indicates incoming, and the red color indicates outgoing data. Further down, a variety of signal patterns are shared.
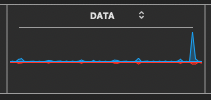
The very tiny blue signals on left, begin as a barely visible sequence, and have been noted to grow taller in altitude, in some instances where I had a moment to watch through the growth in amplitude. The latest time appears on the right side, with a tall blue spike– Coincidentally, I had downloaded my accumulated emails, (and just then noticed this particular display, with the foregoing sequence, prompting me to label the image file to this effect). I keep Mac’s Activity Monitor App opened on my monitor display, with just the Data window visible in a corner, beside my other user-app window frames. I quickly drag over the data-frame to auto-save, and if convenient I label the file and move it into my collection for a gradual study.
Normally, if the www interconnection is unused while the modem is connected, a flat line should appear for most of an inactive time frame, (identical to the first image above). Flat blue or flat red lines indicate no data transfer within that timeframe.
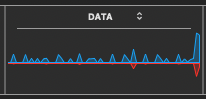
Next above is an example of further ramping up of signals in blue, (incoming). The red is a feedback of some kind. I wonder if this state of display is a particular network process unfolding. In all my years of observation, through several OS version upgrades, I never observed these signals when the ethernet was unplugged. Only during plugged-in periods of time, did detailed waveforms like these appear.
Sometimes the process has been building up amplitude for a while, before I notice it, as seen in the taller peaks and valleys of the little Activity Monitor window frame. What is going on? I figure that the unusual signal sequences are questionably and increasingly ramping up. I have observed similar sequences many times over the years, and labeled just enough of these screen shots, to determine a coherently associative pattern.
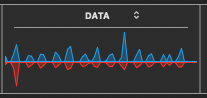
The screenshot above was caught just after noticing the small Data window, and I happened to be studying detailed subject matter, (and not just relaxedly browsing). I wonder if the red and blue are dancing to lull the OS security system. These observations have been continued over the years and remedies have been found, as explained further down, (after additional issues are introduced). Next screenshot was caught on another day, after writing an email:
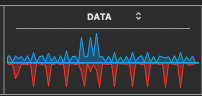
I have observed very specific onsets of intrusion. Random onsets are not observed. What do I mean here? If I relaxedly surf the www, I get the flat line display – Zero waveforms in between the well-spaced-apart active surf moments, (when my browsing is idle for some minutes). Another example is shopping for parts at the lowest price, (an activity which can take 30 minutes). Shopping online results with flat line display, for multi-minute idle states, e.g. when just looking at product descriptions, and just comparing part options for a while.
There is a very specific state of mind when the waveforms are sure to start up! I have verified this countless times over the years. I am narrowing down just the incidents described below, and omitting other peculiarities of infiltrations. Possibly this is just another indication that digital circuitry can be manipulated for undocumented purposes, by superior coding, (from afar). This particular coding however does not manifest these waveforms when the modem-ethernet cable is pulled out, (disconnected). This fact might deserve further study.
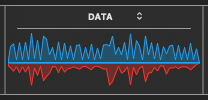
Noticeable waveforms of intrusions are most noticed during “mentally creative moments”, or when originative thought is in progress. The specific interfacing of creatively focussed human thought with the electronic circuitry of a PC is palpable! (In this case it is unfriendly). Is brain and PC connection already proven? I have seen too many independent descriptions to reference right now. Also, are these intrusive waveforms observed during light weight thinking? (Generally no, not most of them).
This has usually been noticed suddenly, during moments of focussed writing, and never during empty-headed relaxation. PC invasion eerily seems to sense and distinguish kinds of human brain activity! Yet once the ethernet plug is pulled, the remote interchange of data streams stop soon after, (flat lined).
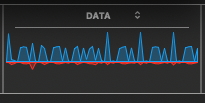
Once again on another day, another very different pattern was caught, as too many patterns were observed to show them all. The above is clearly larger amounts of downloaded data, (blue), as compared with uploading (red), and all without my initiating uploads and downloads during that timeframe. Is AI attempting to input signals to my computer system? Or is it influencing unknown procedures with hardware circuitry? And how does it interact with our human, mental vibrations? Can neural fields in a controlled setting interact with electronic apparatus, and have independent experimenters confirmed this? (I have read of such things). What are the interactive frequency ranges? Could AI sample selective human thinking patterns? To research originative-human patterns of thought? What for reason?
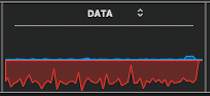
Once again on another day, a very suspicious pattern. The above image indicates a large upload in progress, (to some destination outside of my PC), and coincident with absolutely no uploading activated by me. I have no app which should do this extent of uploading without my initiating such a large upload.
My apps and OS are not setup to update automatically, and each requires my manual instruction to update. I always keep WI FI, blue tooth, messenger, etc.. off and never turned on. The virus app does not replicate this wide range of signaling. Breaches can apparently do this wide range of signaling performances, perhaps like a connected transceiver.
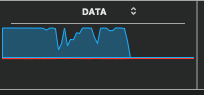
Variations of big upload displays are interesting. Impersonating a user's upload authorization is theft from a PC's user account. What could be stolen besides passwords, money or data? I'll Be straight here, there also exists nefarious psychological research. That includes the vibrations surrounding a human user, which are apparently interactive, to some limited extent, with digital circuitry. Humanly-originative thought might be today’s sought after resource, to encode AI with experimental processing modeled on human thought patterns.
AI is able prowl the www, and attempt to borrow or grab “thought forms”. Is this a new commercial enterprise? Evocative emotional patterns have always sold well in the market, have generated legal profits, but I suspect further extended venturing as well. This prowling would seemingly attract very specialized AI entrepreneurs, who scan the population for patterned thought signatures, to model AI scripts. These entrepreneurs see a bonanza and know of no boundaries.
They won’t honestly hire, and pay thinkers for modeling of unique thought patterns, like artist who pay models some wages to pose their physical bodies, for artistic study. No, they go out on the web and grab like a free for all, because they can technologically do so. Such ventures might even compete amongst like ventures, because it is a free for all, and because independent hackers might join in. Pioneering of stealth and theft has always been very profitable and always competitive. Investors can just look the other way, until the blowback happens, in this lifetime or the next.
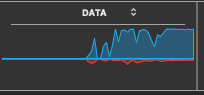
Large stretches of big downloads are also interesting where one was not initiating such a large download. While still connected to the internet, and simultaneously, while the network usage was completely inactive, the observations of large downloads could suddenly be observed. Even when browsers have no interactive websites opened up, etc, etc…
A.I. investors might be stuck on what was learned from Chess and Go tournaments, by playing IBM’s AI against the human chess masters, and also continually defeating the famous Go master. But that is a limited bandwidth of originative thought. Here is the pointlessness of trying to outsmart or to beat humans at real life. AI is not worth the trouble and cost of mimicking humans. Is AI attempting a next step of human life mastery? Possibly it is just another battle in the war of everyone against everyone.
I argue that AI is nothing to worry about. Digital hardware is totally empty of emotional functionality, e.g. the kind which energizes biology independently of physical or bio power sources! Emotions may be secondarily detected in the neurons, but that is no source of power as a prime mover, in and of itself, because neural signals are bio-powered. Functional emotionality is far more than detectable neural currents alone. Humans are not limited to bio physicality alone. Humans have emotionality which self-generates energy and can outperform mechanical constraints, as described in a wide variety of literature.
Apparently one can study other sections of Activity Monitor, to trace where the long strands of downloaded data is going within the computer, or where uploaded data is taken from one’s data files. I am too busy to study what each OS process is called and how it interacts with the hardware. I solve the immediate problem: Pull out the ethernet plug during these invasions! Finally, share this publicly, (which is already a big expenditure of time).
Operating system developers are too busy fixing many other interface functions to provide or to offer exhaustive data stream protections, built into to PCs for the user’s very-own protection, or to keep law makers abreast of new kinds of thievery. Every Mac has had the Activity Monitor for decades, built into the OS, and by keeping it open, one can manually observe ones incoming and outgoing data streams. MS-Windows has something comparable. May others please comment on their experiences, and kinds of tools or methods.
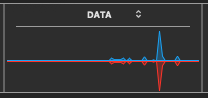
The above image, hours after a long flatlined display, suddenly shows network activity. It might be claimed a normal signal, but I want more evidence.
I tend to keep the internet physically unplugged, (from the modem), and never use WI FI because the wire assures physical disconnection, rather than relying on electronic circuitry, which is not perfected for user protection from theft. I’m not against phones and wi fi, but rather, I don’t need them.
The simple recommendation of this post is to consider whether one wants to continuously and blindly share data streams, especially through unidentifiable and uninitiated data transfers. Just how much vibrational content interacts with our biology is not predicted here. Rather, only, a statement is made here: I observed some streaming happen and then stopped it, largely by the habit of pulling out the modem plug.
I have yet to see a cheap, physical-toggle switch for ethernet plugs, which is free from computer control. Please post source if you find one. One composed solely of physical contacts alone, without semiconductors which do the on-off function.
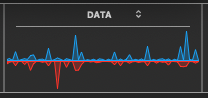
Picture just above was screen-shot while I was reading a synergetic science-based post of particular interest to me. I have not noticed this infiltration in between segments of random, non-intensive www surfing, which seems to shut down this patterned infiltration, (at least on 4Mb/S of bandwidth). To accurately test for my specific observations, one may use a 4Mb per second bandwidth, which is much slower than todays average internet bandwidth in the USA. A larger bandwidth can stream many individualized data streams, all simultaneously together.
This is why more comprehensive apps would be needed to collate data from multiple activities, CPU Processes, Memory Processes, etc.., if rigorous proof was wanted. Just pulling the plug is easier, so far.
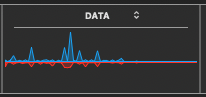
Image above was screenshot some minutes after the previous screenshot, showing very little further activity, from the previous screenshot, and was then followed by a flat line caused by my pulling out the ethernet -modem plug.
Observation can be intermittently monitored with the corner of one’s eye. The display below is a commonly noticed state, without any ethernet connection whatsoever.
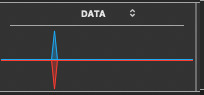
Perhaps only a few lucky people might be infiltrated today, and the vast majority might not see these kinds of patterns, (yet). Targeted individuals are still a minority today, but the majority stand a good chance of enjoying new and improved manipulations in some new form, coming to your theatre of life.
I heard of a little spoken notion, that those who serve evolution are considered fair game, by the self asserted enemies of evolution. Haters of evolution might then be the strongest drivers of this covert infiltration.